Recently there's been reports of what some call OpenPGP Certificate Flooding and others call key poisoning.
For privacy reasons, I have eliminated key server lookups in my email client for years:
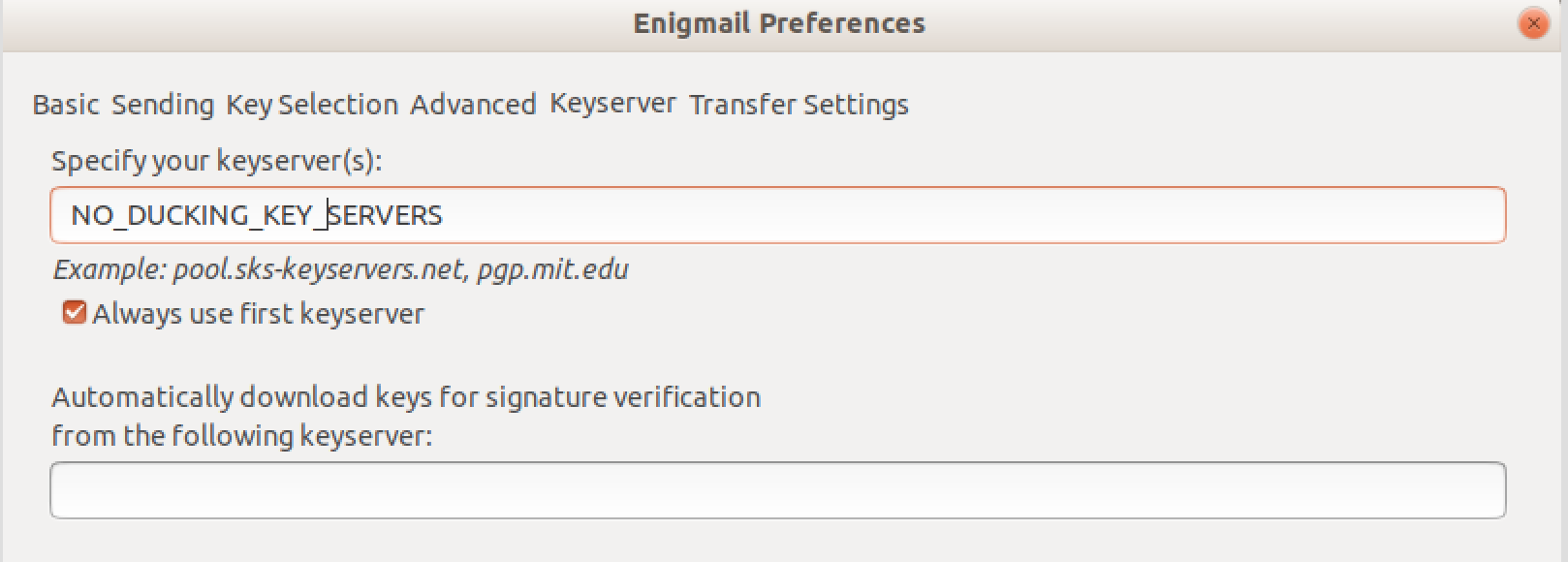
I didn't give much thought to the PGP keys and key servers used for code signing until an incident in our office yesterday.
Turns out there are at least three other configs I could have altered to prevent key server access - or set to a constrained keyserver like keys.openpgp.org. https://keys.openpgp.org/about is controversial. Maybe the final solution is a local moderated keyserver that can collect from external sources but won't subject enterprise employees to updated keys until they pass local policy.
Even if you have never touched an encrypted email, chances are you have computers automatically utilizing PGP to validate packages. Software like Tor or node.js may be configured by default to check for updates at start up. One of the steps may be a PGP validation, including a key revocation check and retrieving the current version of the desired public key.
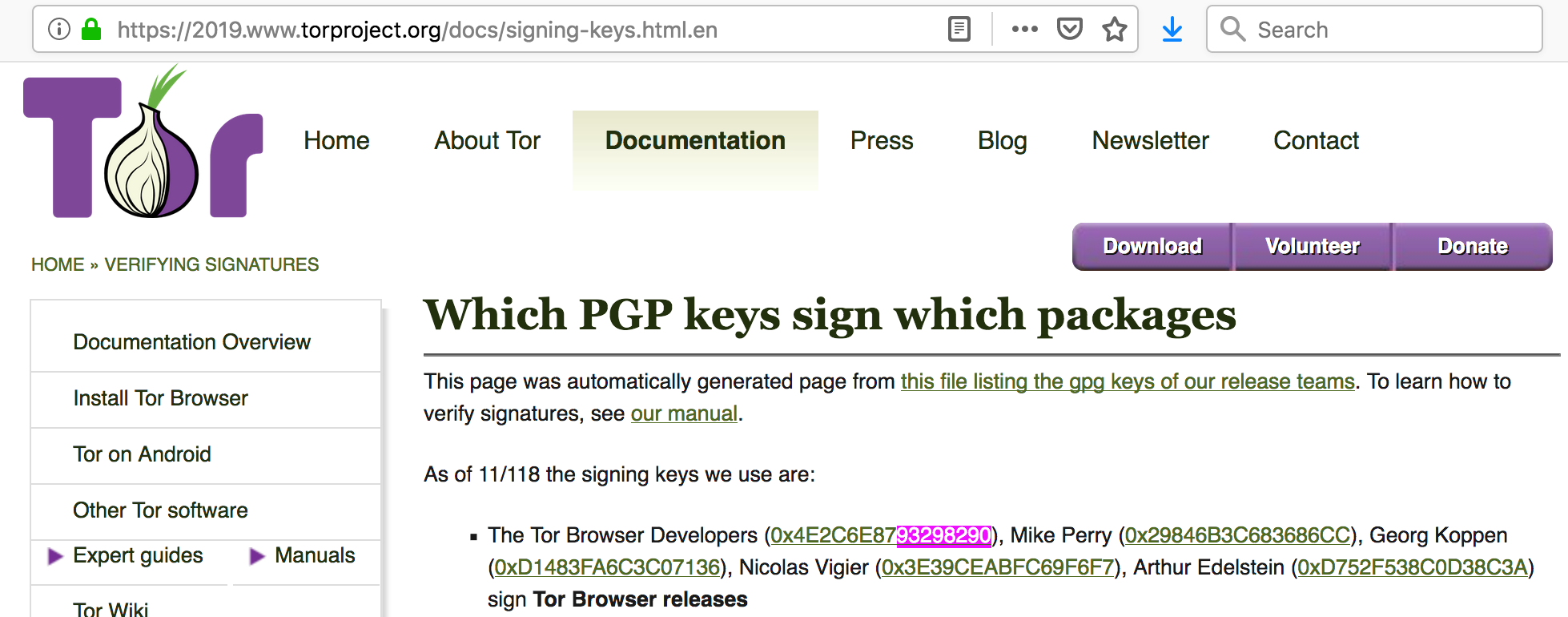
Node.js even officially recommends the sks-keyservers.net (NOTE: we have not seen a flooding attack on the node.js signing key)
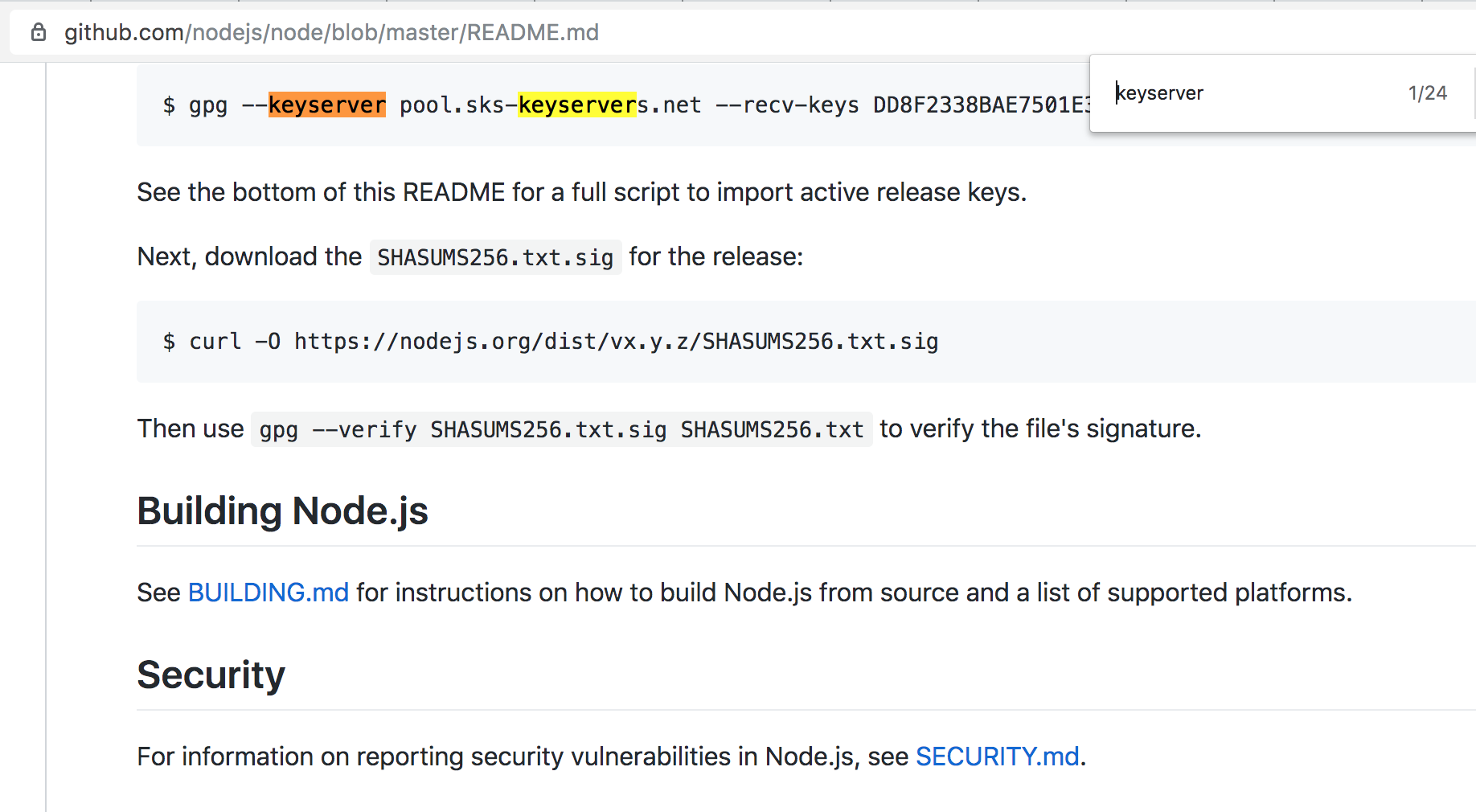
When things go well all this takes place smoothly and automatically. But what if a malicious actor could add say 75,000 bogus signatures to the PGP key used to sign the code you are running? Signing someone else's key is considered a positive by many PGP afficianados - that's what makes this attack work. This capability is considered normal, a feature - not a bug.
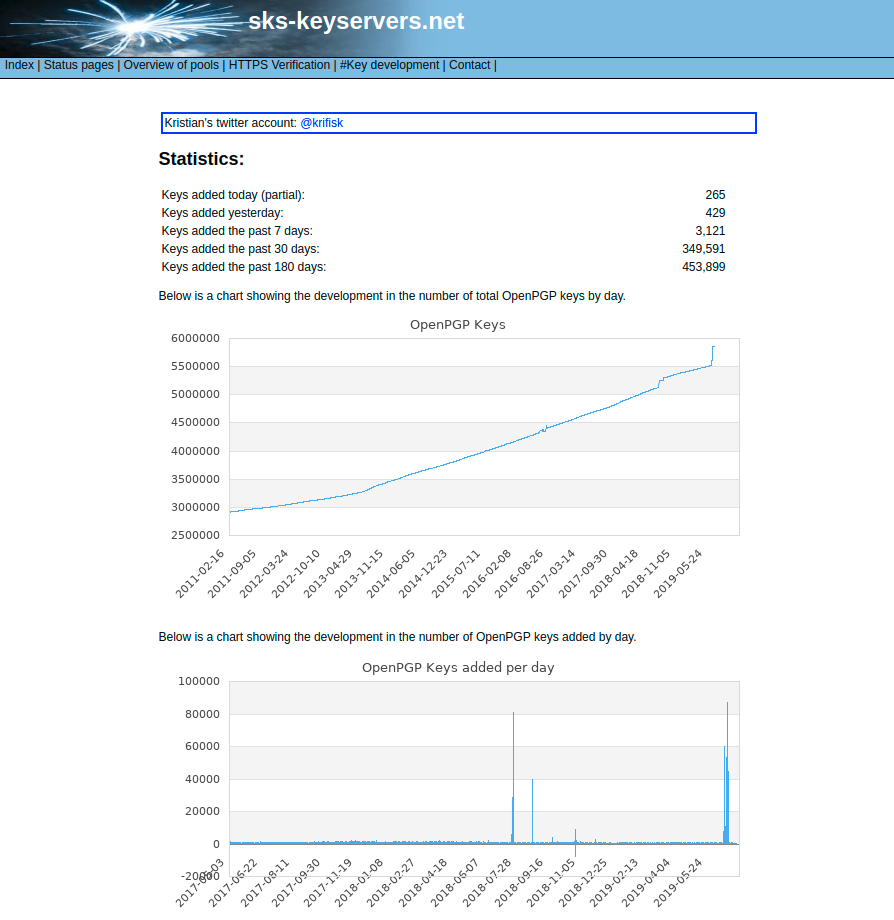
The SKS keyserver has a helpful graph showing a recent spike in key uploads:
What we experienced was that starting up Tor dutifully downloads an updated key with 20 MB of bloated bogus signatures added, from the beleagured SKS key server involved in multiple key flooding / poisoning attacks lately.
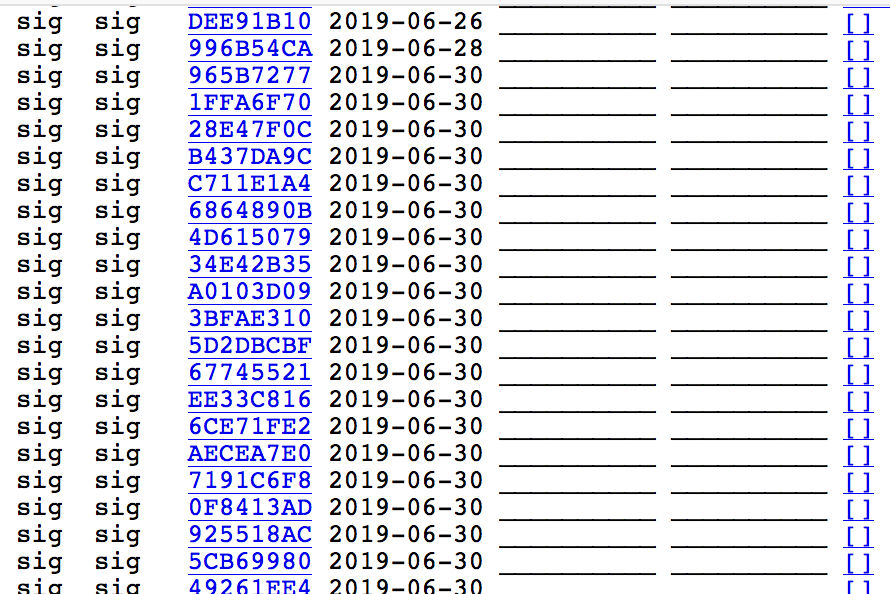
When the new bloated pubring.gpg is parsed for any purpose the computer slows down and crashed a process - which is what led our employee to investigate. See for yourself the estimated 75,000 bad lines added to the offical tor project signing key, as found on the SKS keyserver: search-of-bloated-keyring.html (warning: 19MB html file)
In case you don't want to look at the 19MB list, here's a screenshot. Most of the malicious added sigs were dated June 30th 2019:
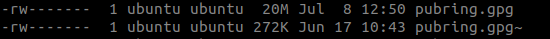
pubring.gpg grew from 272K to over 20MB:
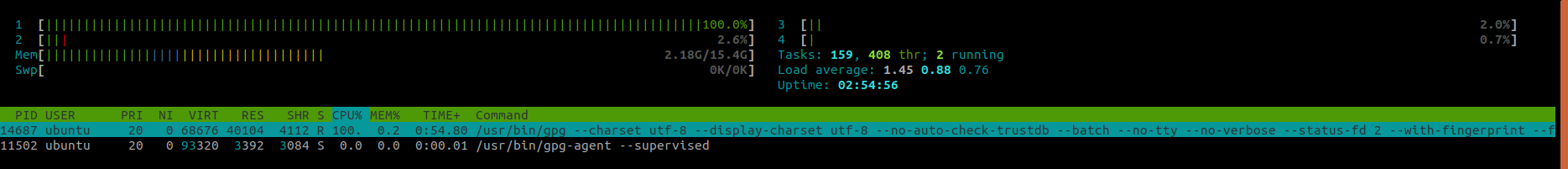
CPU at 100% trying to parse the bloated keyring:
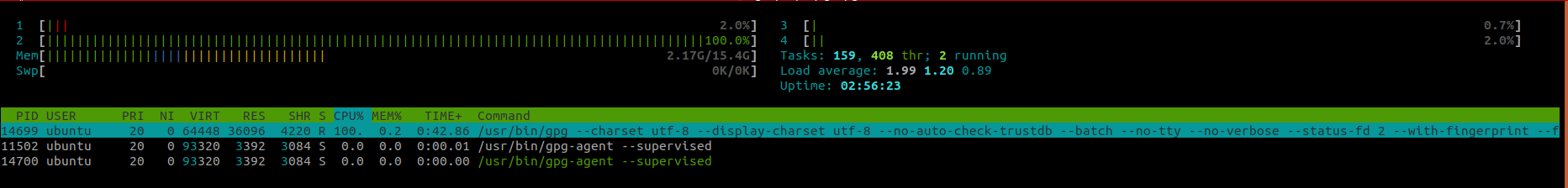
After killing the first process that was at 100%, a second process started and went straight to 100% CPU.
The gpg.conf file on an Ubuntu 18.04 desktop:
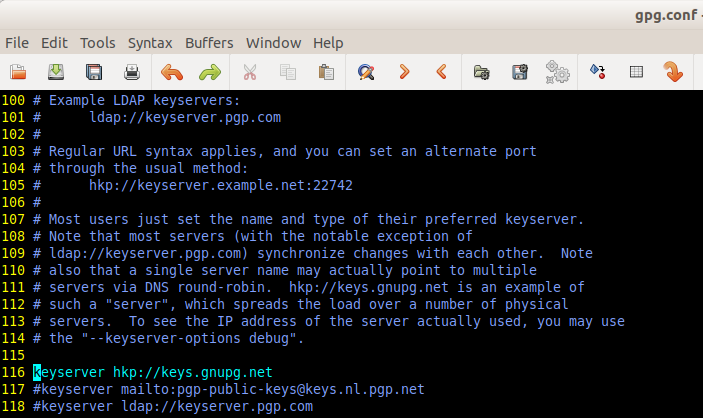
Another place to set keyserver use in the Seahorse email client.
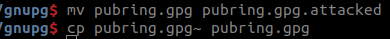
We saved the bloated pubring.gpg file for further study, and restored the latest backup using the copy command.
The employee this happened to runs Ubuntu desktop. I am a Mac user. I edited my
.gnupg/gpg.confand searched for keywords "retrieve" and "keyserver" to find the settings I wanted to adjust. Note that's just for my personal radical brand of privacy. You may have reasons you need to keep the default settings.
 Founder April Lorenzen | Zetalytics serves the enterprise, government, law enforcement, and security industries. We offer unrivalled geographic diversity and exclusive global network visibility in searchable datasets for use by cyber security analysts. Our team has grown over the years by mentoring youth and cultivating age and wisdom, selecting only a certain kind of person - perhaps best described as dedicated, DNS-obsessed oddballs. As a result, our threat intel feeds are unlike any other and consistently protect customer networks from stealthy malicious domains on first sight. Zetalytics Security Feeds integrate easily into existing network protection hardware such as firewalls and SEIM, pushing extra protection near real time. Forensics, incident response and threat intel teams will benefit from the massive historical search API as well as the use of Zetalytics data tools. Advanced trainings are conveniently located between New York and Boston. |
JSON API Access
Get Datasheet
Try Out Tools
5600 Post Road #244
East Greenwich RI
USA
+1(401) 227-4112

